Audit events now available in Cloud.gov logging system
Audit events are recorded by the Cloud.gov platform to track activity against any resource (e.g. users, services, apps, organizations, and more).
While audit events can be queried from the platform via an API, they are only retained by the platform for 31 days by default.
To simplify customer access to audit events and to satisfy M-21-31 guidelines for the retention of these logs, audit events are now available in the Cloud.gov logging system.
Using the Audit - Overview dashboard
A quick way to view audit events is to:
- Log in to the logging system
- Click on “Discover” in the left sidebar menu
- Enter “Audit” in search bar, as shown below,
then follow the link for “Audit - Overview”
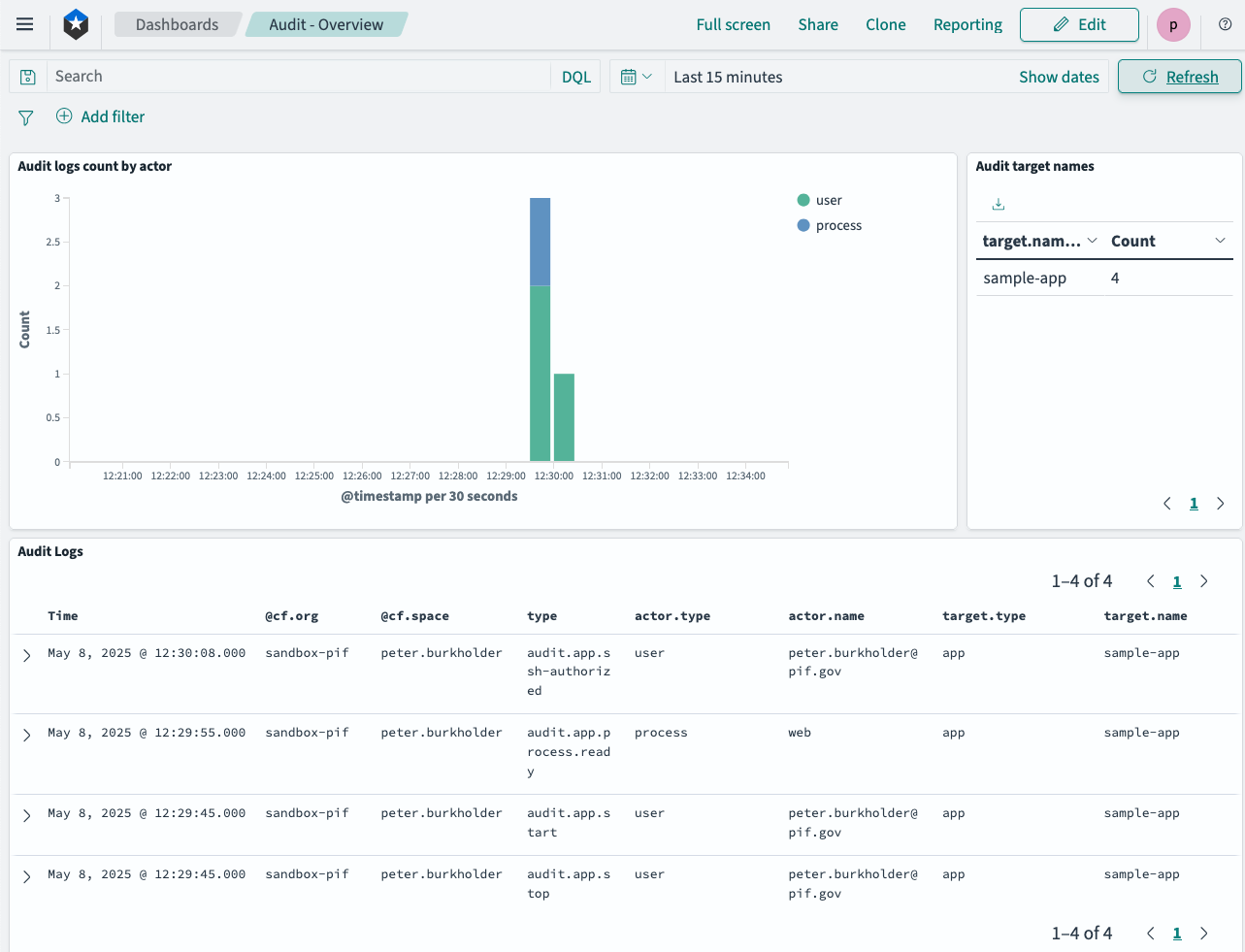
The example “Audit - Overview” dashboard below shows sample audit events for restarting an app, and then SSH’ing to it. When using this dashboard, bear in mind that events may be delayed by 15 minutes.
How to search audit events in the logging system
Audit events are all ingested into the logging system with a value of @type: audit_event , which provides an easy way to filter for them.
To find your audit events in the logging system:
-
Log in to the logging system
-
Click on “Discover” in the left sidebar menu
-
Add a filter for
@type: audit_eventto your log search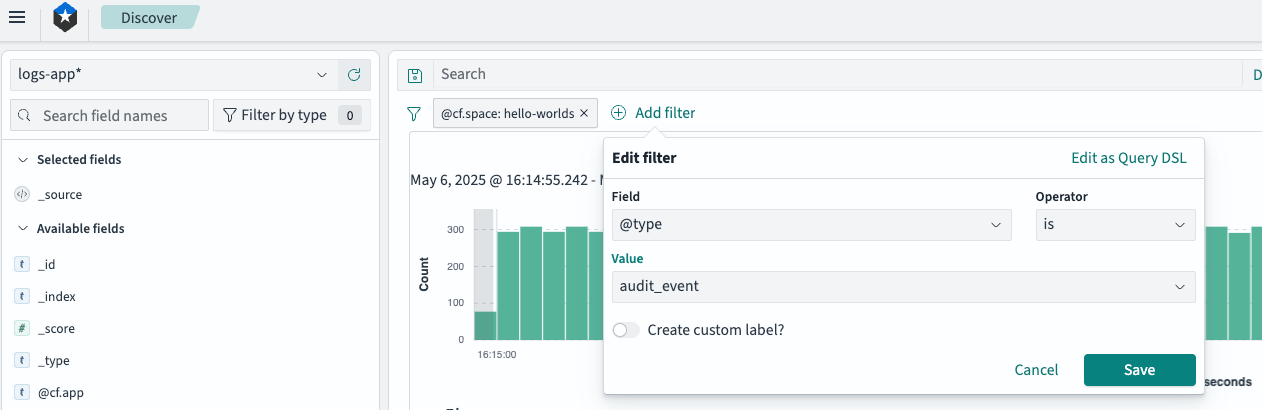
-
Adjust the view of the results as desired
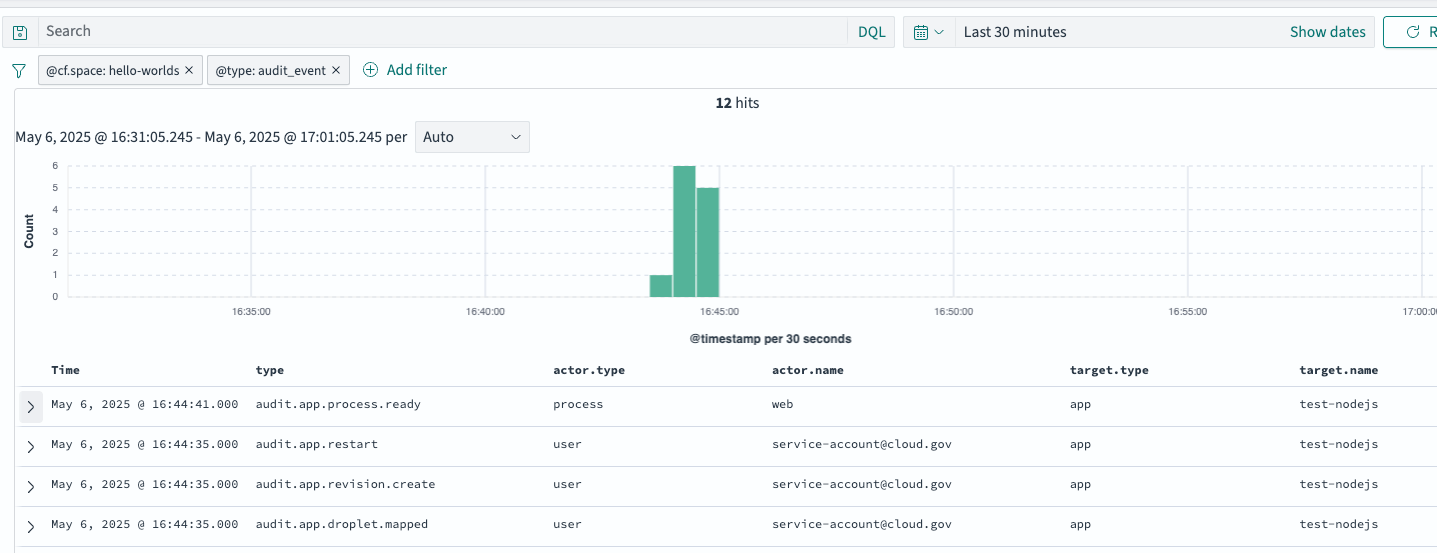
-
Apply additional filters on the audit event fields as desired. For example, to filter for app restart events, add a filter of
type: audit.app.restart: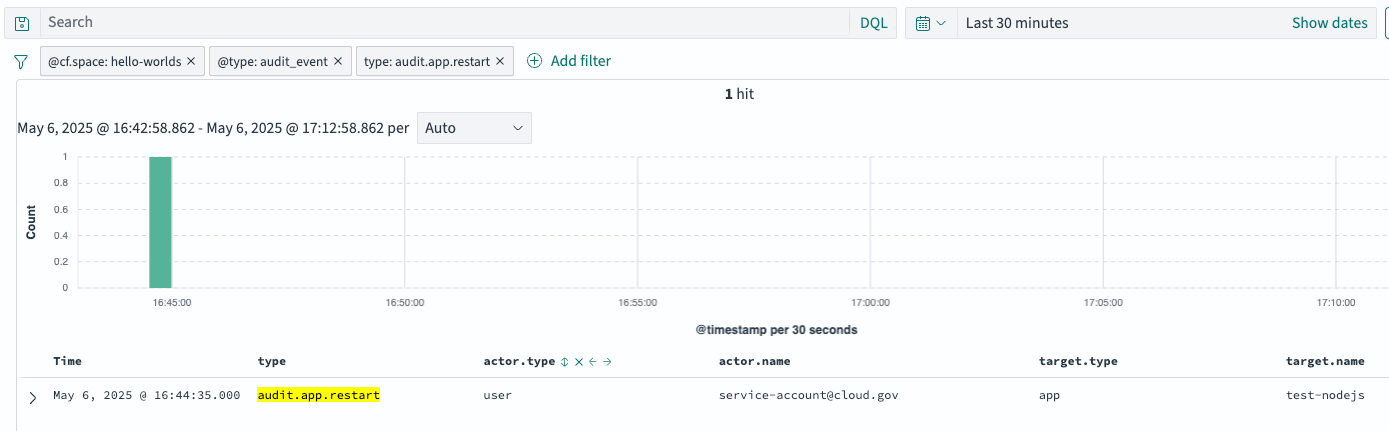
Audit event fields
The fields available on audit event records are:
guid- GUID for the audit eventtype- the type of audit event recordedactor.guid- GUID of the actor for the eventactor.type- Type of the actor for the event (e.g. user, process)actor.name- Name of the actor for the eventtarget.guid- GUID of the target for the eventtarget.type- Type of the target for the event (e.g. app, service)target.name- Name of the target for the eventdata.*- Additional information about the event. The fields are different for eachtypeof event.created_at- Time when the audit event was createdupdated_at- Time when the audit event was last updated
How audit events are ingested into the logging system
An automated job runs every 15 minutes to pull the audit events from the platform and ingest them into the logging system. Thus, there could be up to a 15-minute delay before any audit event logs appear in the logging system.
Retention
Audit events are retained in the logging system for 12 months and in offline storage for an additional 18 months.
Relevant NIST controls
Audit events stored in the logging system satisify NIST controls in the AU control family, specifically:
- AU-02
- AU-11



