How cloud.gov continually adapts to dynamic cybersecurity threats
Managed Information Security
Government web applications and services are targeted by a barrage of ever-increasing challenges, probes, and malicious traffic. These attacks try to exploit common vulnerabilities, compromise infrastructure, or disrupt services for legitimate users. With thousands of customer application instances running on cloud.gov, we see many different kinds of attacks. Our commitments to safety, security, and transparency ensure that our defenses are up-to-date and robust, safeguarding cloud.gov customer applications from the impact of high-traffic-volume attacks directed at both the platform and our agency customers.
One of cloud.gov’s priorities is to make sure that agencies can focus on their core mission without the burden of dealing with the complex and changing discipline of web application security. We ensure that all customer apps on cloud.gov are protected by a strategic collection of web application security best practices developed to combat the kinds of threats that government websites are uniquely prone to experience. These strategies are part of our more complete security posture, which is continually emerging and evolving in response to the malicious actors and the attacks they attempt.
cloud.gov’s Web Application Firewall (WAF) stands as one protective barrier against various cyber attacks, operating between a web application and the internet. It acts as a vigilant gatekeeper, monitoring, filtering, and blocking malicious HTTP traffic, while allowing legitimate traffic to access appropriate resources. A specific set of WAF rules define the criteria for allowing or blocking incoming requests to all cloud.gov managed websites and applications.
Challenge Requests and Rate Limiting
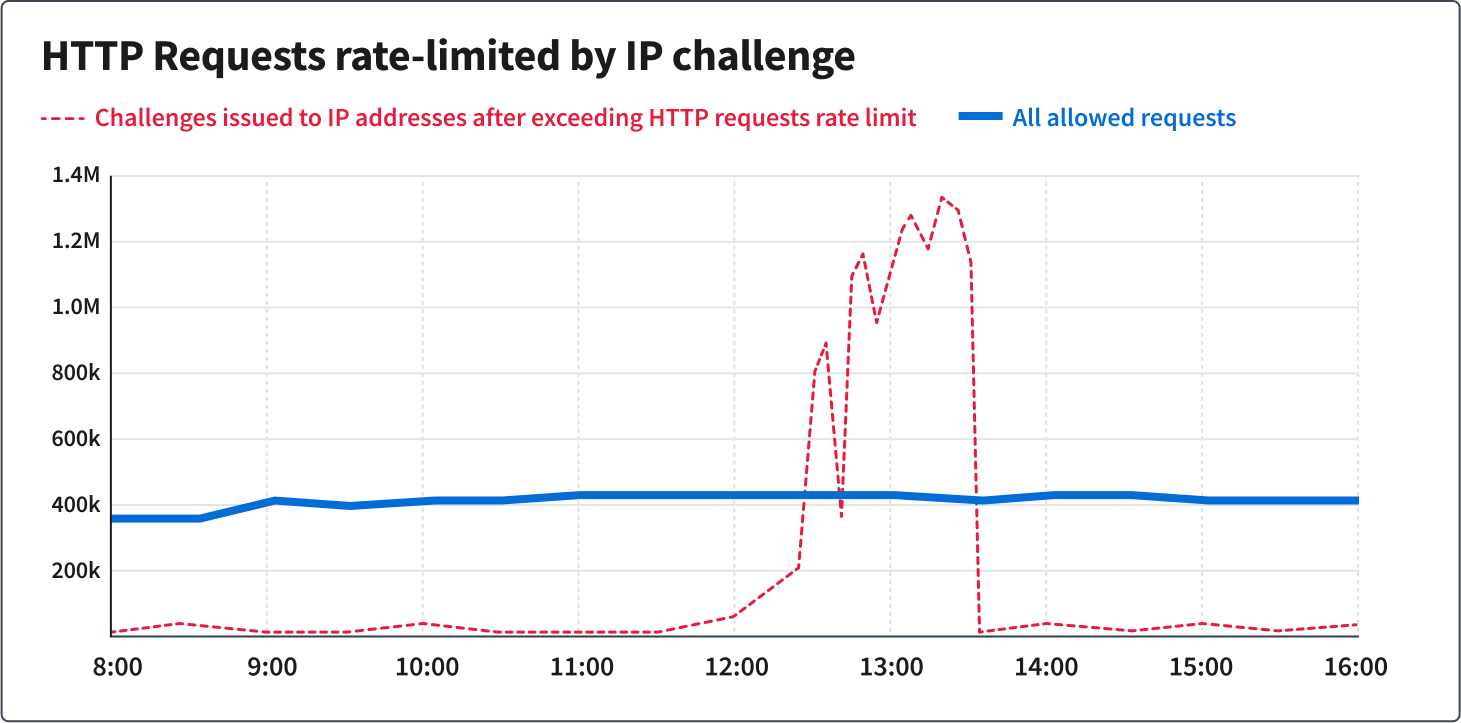
In order to make sure that an HTTP request to access a given web application is a legitimate visit and not a bot, cloud.gov issues a silent browser challenge. It’s similar to a CAPTCHA, but doesn’t require the visitor to successfully solve a puzzle, as it runs in the background of the browser. This approach helps implement effective rate limiting, managing spikes in requests during high-traffic events, and separating legitimate traffic from probing or DDOS-style attacks. cloud.gov’s WAF rules also make sure that a single IP address can pass no more than 2,000 of these challenges within a 5-minute period, so that even as malicious attacks become more convincing, customer applications on cloud.gov remain available and responsive.
After implementing these WAF rules, we monitored traffic surges to ensure that the change handled situations resembling these types of attacks without any negative impact to cloud.gov customers. For example, consider this graph of traffic across the entire platform from November 7th, 2023:
Reputation Lists
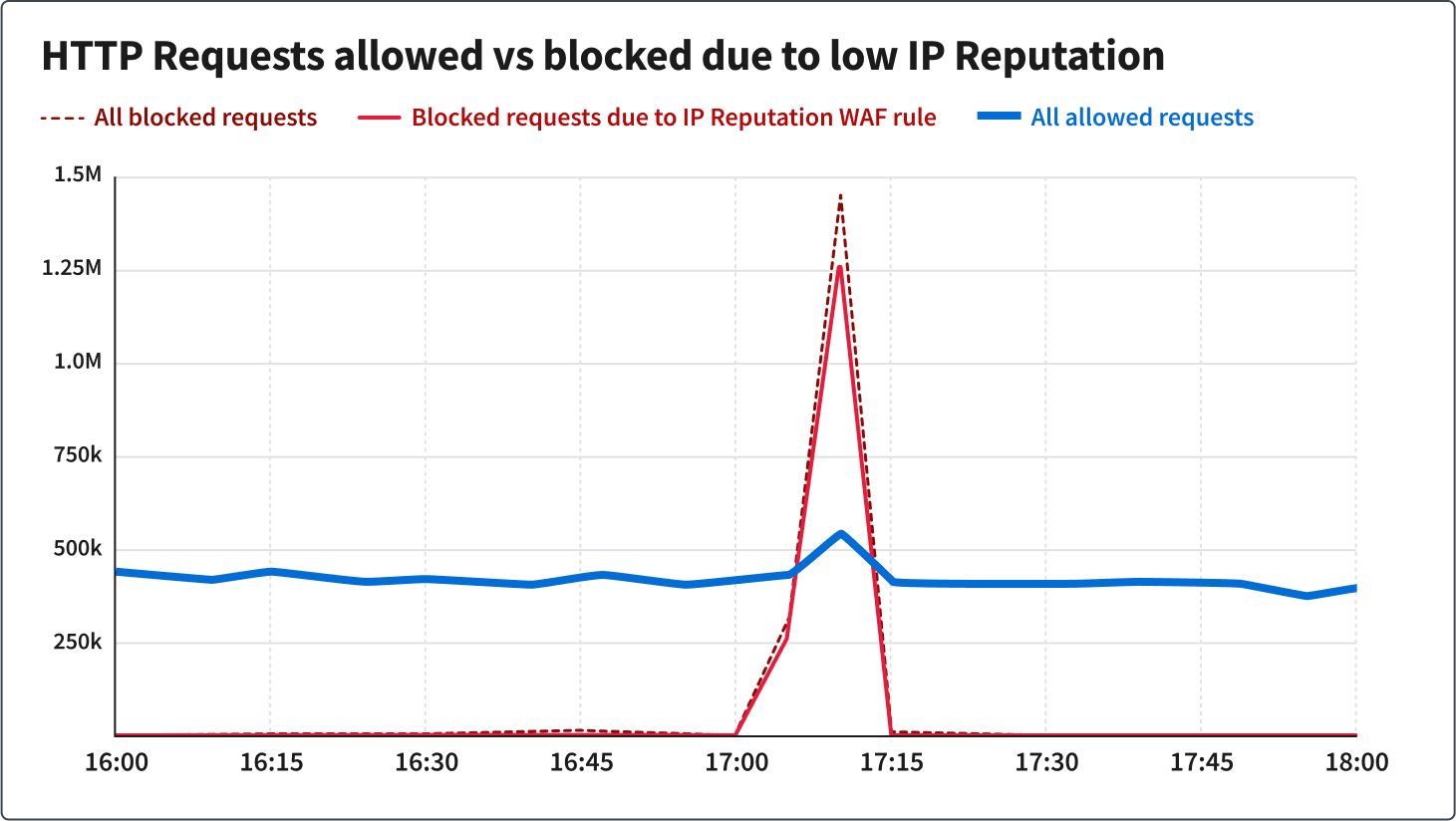
Another element in cloud.gov’s WAF strategy is the use of existing reputation lists to exclude known potentially malicious or automated traffic that originates from specific IP addresses. At times, traffic surges to customer applications come from IP addresses that were previously determined to be bots or other threats. cloud.gov protects all of our customer applications by blocking traffic from these known, low-reputation IP addresses. We monitored a potential attack from known low-reputation IP addresses on the evening of November 3rd, and despite seeing more than one million requests in a span of 15 minutes from these IP addresses, the reputation list WAF rule blocked the vast majority of the potentially malicious traffic:
Just as the cloud.gov web application security approach guards against known threats using adaptive reputation lists, the cloud.gov team flexibly and skillfully reacts to new situations. Real-world incidents, like a surge in potentially malicious traffic experienced last October, serve as valuable lessons for how cyber threats are changing for government web applications. Our team not only responds quickly during these incidents but actively works on proactive measures to prevent future occurrences. This iterative process of learning and improvement ensures that our security measures adapt to emerging challenges. We publish updates like these to reflect our total commitment to providing a resilient and reliable platform for our users.
Operating as a public entity in the government space means that malicious actors will regularly attempt to disrupt the services being provided to customers and stakeholders or to compromise the underlying infrastructure. At cloud.gov, we strive to make sure agencies can trust that their applications are in capable hands, allowing their teams to focus on innovation and development while we handle the rest.
If your development team is interested in hearing more about cloud.gov, scheduling a demo, or getting access to a free sandbox, email us at inquiries@cloud.gov.


